What is armitage? Armitage is a graphical tool to automate metasploit attacks, very useful when performing a penetration to a server, and that at the time of scanning a target tells you are what exploits could be used against the target, has many more options that will explain later.
TUTORIAL:
First we get the IP address of our victim, through a ping your web server must open a terminal and ping it to the web page.
# Ping www.paginaweb.com
Which will return the IP (72.32.231.8) server where the website is hosted.
Then we will work directly with Armitage, for it will open another terminal and start the armitage
# Armitage
We will let you connect
This tells us that the rpc server is not running and start it asks if you want us, we give yes and began to start, if it is the first time they occupy armitage be delayed a bit to connect.
Well once opened go to Hosts / Add Hosts ...
We enter the IP address and give it our goal to Add
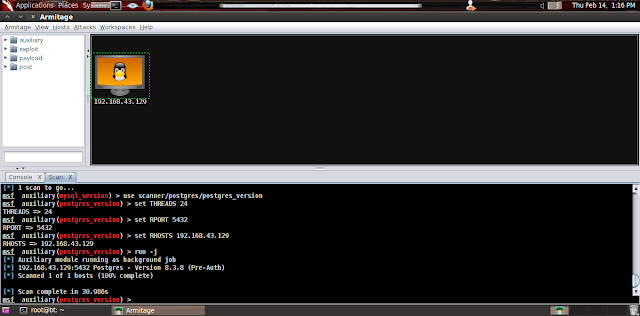
adhere once they leave the IP address of a monitor icon and the IP below, we click right click and scan for the server Carries a scan, the scan will tell us which ports are open, that operating system is that service is installed and running by the ports, etc ...
We wait for the scan completes.
As you can see from the image server is linux, if you climb to the top we can see the ports that are open.
Well go on, go to attacks / find attacks, to see that attacks could be used against the target and hope we click as it takes a while, once we will get a box saying the attacks scan ended.
Once the scan possible attacks we click right on the target and we will get the list of all possible vulnerabilities to exploit, if set then an option to test the exploit served with the vulnerability found (check exploits) but not all support this option exploits.
They give check exploits to try, this is the best part of armitage and it saves us time testing exploits go one by one, tested good if served exploits and none can keep trying with the different services.
(The goal is not exploitable)
as we found a vulnerability can be exploited to target :) go back and give
right click attack and vulnerability we found in this case(tikiwiki_graph_formula_exec) and we click, we will open the console where we can configure our exploit.
We give Launch to launch the exploit, once ready the exploit will give us the option to open a shell to the server and our aim icon rays will break out in the purest style of a hollywood movie xd hackers.
is the option to upload a file could climb a backdoor if we maintain access to the server, a Trojan or keylogger, there depends on the intentions they have, but for now we'll leave it up here.
























I want to shear a life changing story with everyone who cares to read this testimony. Blank atm cards are real and are effective all over the world. my name is Gorge Judy i live in SPAIN . I got this card from [skylink technology] a month ago. this card has really help me pay my debts and now i am free from all financial problems. I no this is hard to believe , but i never knew there was this kind of card until i got one. This card withdraw more than €6000 daily and it is very easy to use. But you have to be very careful in other not to be caught by the police because it is illegal. If you want more information on this card and how to get one just contact the hackers by this address skylinktechnes@yahoo.com or whatsapp +1(213)785-1553 or website: https://skylinktechnes.wixsite.com/info
ReplyDelete